What is KMS (Key Management System)?
AWS KMS (Key Management Service) is the service that manages encryption keys on AWS which makes it easy for you to create and control the cryptographic keys used to encrypt your data. AWS KMS provides a more robust, secure, and scalable solution for managing encryption and decryption, especially for applications that require stringent security and compliance measures.
KMS offers centralized and automated key management it reduces the risk of key exposure and mismanagement by securely storing keys and KMS supports automatic key rotation for CMKs, which helps enhance security by regularly updating the cryptographic keys. The important thing is it provides detailed logs of key usage through AWS CloudTrail which allows for monitoring and auditing of all key management activities. KMS can handle a large volume of encryption and decryption requests, it easy to maintain applications with cryptographic operations. Also, the AWS takes care of the backup and recovery of keys, ensuring they are always available and protected against data loss.
Customer Master Key (CMK)
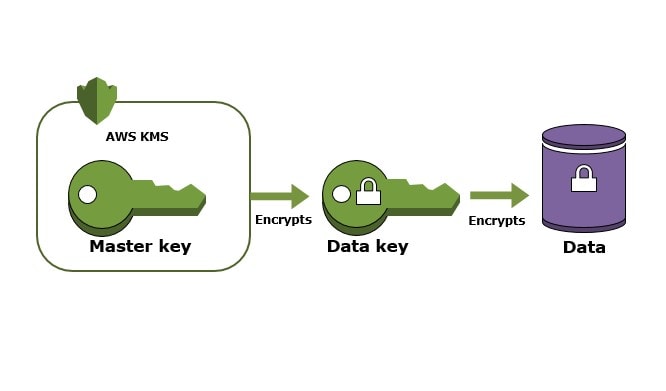
Customer Master Key (CMK) is a core concept in cloud-based encryption services, such as AWS Key Management Service (KMS). It is a cryptographic key that is used to encrypt and decrypt data, providing a secure way to manage the encryption of sensitive information in the cloud.
- CMKs are used to encrypt small amounts of data directly which can only encrypt a maximum of 4KB data. For larger data, the CMK is used to generate a Data Encryption Key (DEK), which can then be used to encrypt larger data sets.
- CMKs are managed by the KMS and particular CMK generate Data Keys (DKs) for encrypting large amounts of data. We can generate multiple data keys from one CMK.
- When encrypted data is received, the CMK (or the DEK generated by the CMK) is used to decrypt the data, making it readable again.
- With customer-managed CMKs, you can monitor usage, define permissions, and rotate keys as needed. AWS KMS provides a centralized place to manage all your keys.
- AWS KMS can automatically rotate customer master keys (CMKs) every year. When a CMK is rotated, AWS KMS generates a new cryptographic material for the CMK but keeps the same key ID. This means you can continue using the CMK without any changes in your application.
Data Keys (Data Encryption Keys)
Data Keys or Data Encryption Keys (DEKs) are cryptographic keys used to encrypt and decrypt data. Unlike Customer Master Keys (CMKs), which are designed to manage and protect encryption keys securely, DEKs are specifically generated for encrypting large amounts of data, such as files or database entries.
The Process of Using Data Keys:
- Generate the Data Key:
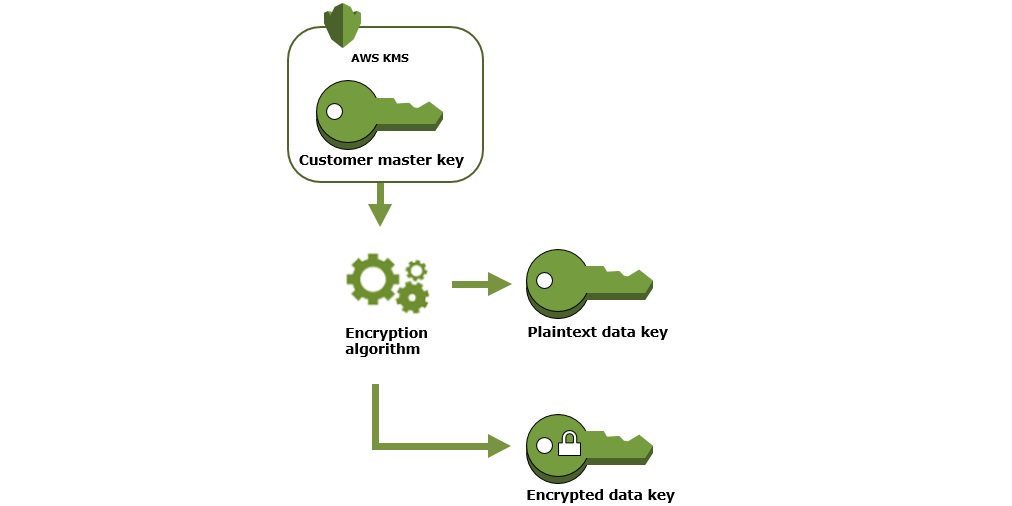
- A CMK is used to generate a DEK. This is done by calling the cloud provider’s key management service (like AWS KMS) with a request to generate a new data key.
- The response includes both a plaintext version of the DEK (for immediate use) and a version that is encrypted with the CMK (for secure storage).
- Use the Data Key for Encryption:
- The plaintext DEK is then used to encrypt the actual data (e.g., files, database records).
- Once the data is encrypted, the plaintext DEK is typically erased from memory to ensure it cannot be accessed by unauthorized users.
- Store the Encrypted Data and Encrypted Data Key:
- The encrypted data is stored along with the encrypted version of the DEK.
- The encrypted DEK can be safely stored alongside the data because it can only be decrypted by the original CMK.
- Decrypt the Data:
- To decrypt the data, the encrypted DEK is first retrieved and sent to the key management service to be decrypted using the CMK.
- The key management service returns the plaintext DEK, which is then used to decrypt the data.
Encrypt with Data Keys
Encrypting data using data keys involves a two-step process to ensure that sensitive data is protected while also enabling efficient decryption when necessary. Here’s how it works, specifically using AWS Encryption SDK or OpenSSL:
Step 1: Generate a Data Key
In AWS, you would typically use AWS Key Management Service (KMS) to generate a data key. The KMS service provides a plaintext data key and an encrypted version of the data key. The plaintext key is used for immediate encryption of data, and the encrypted version is saved securely
Data Key Components:
- Plaintext Data Key: A raw encryption key used to encrypt data.
- Encrypted Data Key: The plaintext data key that is encrypted using a master key, which can be managed within AWS KMS.
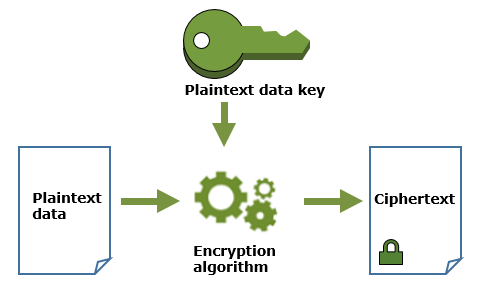
Step 2: Encrypt Data Using the Plaintext Data Key
Use the plaintext data key to encrypt your data. You can use encryption libraries, such as OpenSSL or the AWS Encryption SDK, to apply symmetric encryption (like AES) to your data.
- With OpenSSL: Use AES encryption with the plaintext data key to encrypt your sensitive data.
- With AWS Encryption SDK: The AWS Encryption SDK simplifies the process of encrypting and decrypting data with data keys.
Step 3: Remove the Plaintext Data Key
Once the data has been encrypted using the plaintext data key, you must remove the plaintext key from memory. This step is crucial for security to ensure the key is not exposed or retrievable.
Save only the encrypted data (ciphertext) and the encrypted data key. The encrypted data key is required for future decryption but is useless without access to the AWS KMS master key or another decryption method.
Step 4: Storing Encrypted Data and Data Key
Store the encrypted data and the encrypted data key securely. When you need to decrypt the data, you will use the encrypted data key, and if you’re using AWS, you’ll call AWS KMS to decrypt it and retrieve the plaintext data key temporarily.
Decrypt with Data Keys
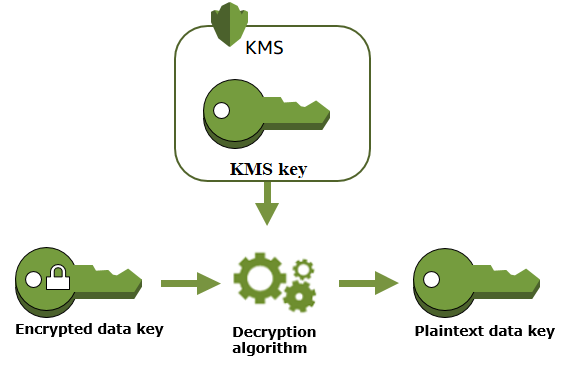
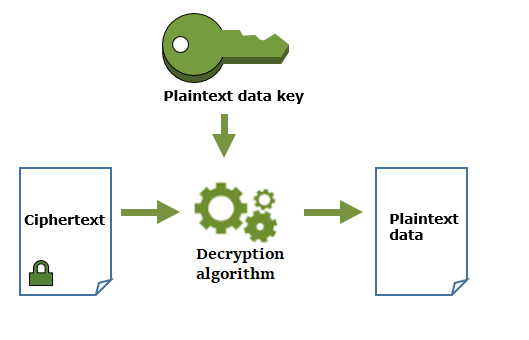
To decrypt data encrypted with a data key, the process involves securely retrieving the plaintext version of the data key and using it to decrypt your data. Here’s a step-by-step explanation of how to handle decryption using the AWS Key Management Service (KMS) or similar techniques:
Step 1: Retrieve the Encrypted Data Key
- When you encrypted your data, you saved the encrypted data key (provided by AWS KMS) along with your encrypted data (ciphertext).
- To decrypt your data, you need to call AWS KMS and provide this encrypted data key.
Step 2: Call AWS KMS to Decrypt the Encrypted Data Key
- Use the AWS KMS Decrypt API to send the encrypted data key to AWS KMS.
- AWS KMS will use the associated master key to decrypt the encrypted data key and return the plaintext data key securely.
Step 3: Use the Plaintext Data Key to Decrypt the Data
- Now that you have the plaintext data key, use it to decrypt the encrypted data.
- If you used OpenSSL for encryption, you would use a similar OpenSSL command to decrypt the data with the plaintext key.
- If you used the AWS Encryption SDK to encrypt your data, you can use it again for decryption. The SDK handles much of the complexity for you.
Step 4: Remove the Plaintext Data Key from Memory
Once decryption is complete, make sure to remove the plaintext data key from memory. This step is crucial to minimize the risk of the key being exposed or compromised.
Conclusion
Using AWS Key Management System (KMS) for data encryption and decryption is a robust and secure method to manage sensitive information. By leveraging Customer Master Keys (CMKs) and Data Keys, AWS KMS ensures that data is protected efficiently and in compliance with stringent security standards. The process involves encrypting data using Data Encryption Keys (DEKs), which are themselves secured by CMKs. This layered approach to encryption provides a balance of performance and security.
When encrypting data, you use the plaintext data key to protect your information, and once encrypted, the key is safely discarded. AWS KMS holds the encrypted version of the data key, which can later be used to decrypt the data securely. Decryption involves retrieving and temporarily using the plaintext data key via AWS KMS to unlock the protected data.
Overall, AWS KMS simplifies key management, automates the secure handling of data keys, and integrates seamlessly with AWS services. This encryption strategy not only enhances data confidentiality but also provides a scalable and easy-to-implement solution for protecting data at rest and in transit. The use of KMS in encryption and decryption processes ultimately gives organizations peace of mind by ensuring their data remains secure and accessible only to authorized entities.